Hvad ville du gøre hvis dit vCenter blev utilgængeligt i morgen og hvilken indflydelse ville det have på din forretning? Svarene falder typisk i to kategorier:
- Mit vCenter er ikke kritisk for min produktion og hvis det er nede installere jeg blot et nyt og forbinder det til mine ESXi servere.
- KRISE! Hvis mit vCenter er nede er der ikke self-service, overvågning og styring af de virtuelle resourser. Jeg er på dybt vand!
Det er er en gammel kendt udfordring i et hvert datacenter. Hvordan beskytter man sin VMware mangement stack og får den hurtigt online igen med en lav RTO. VMware udvider sine management produkter. Hvor man tidligere kunne nøjes med en enkelt vCenter server består de fleste miljøer af adskillige servere til håndtere den daglige drift og rutiner. Den er i dag udbygget til:
- vCenter (med intern eller ekstern database)
- vRealize Operations Manager
- vRealize Automation Center
- vReaize Log Insight
- NSX Manager
- PSC (platform services controllers)
- SDDC (VMware Cloud Foundation)
- Management AD og DNS
Udover disse VMware services er der også flere administrative servere som IT afdelingen er afhængige af som kan tilføjes som kritiske komponenter til en disaster plan. Med det Software Defined Data Center er det ikke som tidligere hvor vCenter var “nice-to-have” – er det nu blevet til en kritisk funktion der altid skal være online. Hvis vCenter er nede skaber det problemer for ting som
- Selv-provisionering af nye virtuelle maskiner
- Overvågning
- 3′ parts produkter der kommunikerer med vCenter
I et tilfælde hvor der er nedbrud eller datatab på management stacken er man ilde stedt. Hvordan bringer man stacken online når vCenter og evt. management AD og DNS er nede? Er din platform til beskyttelse 100% uafhængig af dem? Med stor kompleksitet er det muligt at bygge et system med traditional software som kan håndtere dette. Men hvordan tester man det? Hvordan sikrer man at alle windows servere benytter lokale service accounts og ikke AD konti? På hvilken måde kompromittere dette sikkerheden? Hvad med faren for Ransomware når traditional software kører på Windows og i værste tilfælde bliver backup data kryptereret og utilgængelig?
Til at løse dette er der behov for at se på problemet med friske øjne. Der er behov for en løsning der opfylder følgende
- Baserer sig ikke på Windows og backup data er immutable
- Har ingen afhængigheder af AD og DNS
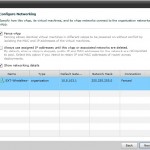
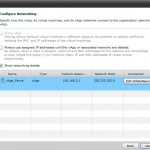
- Kan benyttes selvom vCenter er utilgængelig
- Kan udføre en Instant-Mass-Restore og bringe ALLE administrative servere online med det samme og som en gruppe.
- Simpel og alt inkluderet i et system (ikke 4-5 forskellige produkter og producenter)
- Ingen single point of failures.
Hos Cohesity løser vi dette elegant og din management stack er beskyttet og muligt at lave recovery på få sekunder. De unikke funktioner ved Cohesity:
- Policy baseret beskyttelse
- Alt-i-et-system (de-dupe storage, backup software, databaser, always-online, fuld HA for alle komponenter software og hardware.)
- Instant-Mass-Restore: Recovery af 5 eller 50 maskiner på få sekunder
- SnapTree: Alle backup punkter er fully hydrated og instant-recoverable. Ingen baggrunds IO operationer for at lave syntetiske fulls
- Test/Dev: Mulighed for at teste recovery når som helst og validere det virker
Hvis du ønsker at få en demo at dette i dit eget datacenter så tag kontakt.
Hvis du vil læse mere om hvordan Cohesity beskytter den fulde VMware Management Stack inklusive cloud foundation så læs mere her:
http://www.cohesity.com/vmware-cloud-foundation-vcf-cohesity-white-paper/
Video Demonstration: